Swamp CTF 2025

Messages From The Stars
We recently detected this signal from deep space, we aren’t quite sure what to make of it but we suspect it originated from intelligent life. Want to take a crack at decoding it?
Misc, 28 solves, 193 points
The signal contained sequences of beeps composed of two different frequencies. It could not be Morse code, as it didn’t match any Morse sequence. Still, I converted the signal to binary to get a textual representation of the sequence.
0000000000000000000000000000000000000000000000000001111001111111001111110000000000000000000000000000000000000000000000000000000001000110000110000100000000000000000000000000000000000000000000000000000000000001000001000011000010000000000000000000111001100110001001111001011101110010111000100000000001100001000000000000000000100010010011001001000100110011001001100110010000000000110000100000000000000000010000001001100100000010010001000100100001001000000000011000011111100000000000000111000100101010011111001000100010010000100100000000001100001000000000000000000000010001100110001000100100010001001000010010000010000110000100000000000000000010001000110011000100010010001000100110011000100011000011000010000000000000000000111000011001100011111001000100010010111000001111000000110000100000000000000000000000000000000000000000000000000000100000000000000000000000000000000000000000000000000000000000000000000000000000010000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000011000000000000000111100001111000000001000000000000000000000000000000000000000001000000000000000100001001000010001000000000000000000000000000000000000000000000100000000000000010000100100001000100000000000000000000000000000000000000000000010001111110101100000110000001100111001001011100011111100111000000000000000000001001000100011000001110000011100001000100110010010001000100010000000000000000001000100011001000000000100000001000100010010001101000110010000000000000000000001100001111000100000000011000000110010001001000110001111000011100000000000000000001100100000001000010000110100001100100010010001101000000000001000000000000000000010001111100100001100010011000100010001001000110011111001000100000000000000000001001000010010000011110000111100001100100100011010000100011100000000000000000000101100001000000000000000000000000000000000000011000010000000000000000000000000011011111000000000000000000000000000000000000000111110000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000100000000000000010010000000000000000000000000000000000000000000000000000000000101000000000000010010000000000000000000000000000000000000000000000000000000000100100000000000011110000000111000000000000000000000000000000000000000110000000010100000000000001001100000010000000000000000000000000000000000000000100100000000100000000000000100011000001000000000000000000000000000000001000000100001000000001111111111111010000010011111010110011100010111011100000000101111110010001000000010001000100001011111000001000110001000100110011001000000001000000000000010000001000010001001000000000000100010000100011010001000100000000010101010000000100000011111111111000000000000010001000010000101000100010000000000101010111000010000000010000001000000000000001000100001000110100010001000000000000000000100010000000010100001010000000000000100010000100010010001000100000000000000000010010000000010001001000100000000000010001000001110001000100010000000000010101010001000010000000000000000000000000000000000000000000000000000000000000010101010011000010000000000000000000011111000000000000000000000000000000111110010000000010000010000000000000000000000000000000000000000000000000000000000000000111111110000010010000010000000000000000000000000000000000000000000000000000000000000000000010010000010100000000000000000000000000000000000000000000000000000000000000000010010000010001000000000000000000000000000000000000000000000000000000000000000000000010010101010000000000000000000000000000000100000001111100000000000000000011111001000010001000000000000000000000000000010001000000100001000000000000000010000010000000101000000000000000000000000000001000100000010000100000000000000010000000100001001001000000111100101110001110001110010111000000110010110000000010011111001000011111000000100010011001001000100010001100110001110001100000000001000001100100000010000000000001001000110100011001000100011000000100100000000000100001010010000001000000001111100100011010000100100010001100000011010000000000010001001001000000100000000100010010001101000110010001000110100001101000000000001100000100100000010000000010001001000110100010001000100011011000100100000000000110000010010000001000000001111100100011001110000110010001100111100010000000000111100000010000001010000000000000000000000000000000000000000000000000000000000010011000010000001000100000000000000000000000000000000000000000000000000011111001000111110000001000001000000000000000000000000000000000000000000000000000000001111111000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000001111000011100000000000000000000000110000000000000000000000000000000000000000001000010001000000000000000000000000000100000000000000000000000000000000000000000100001000100000000000000000000000000010000000000000000110011000100111101100010000001101111100111000101101011101110001000000000000000001001100100100010010001000011100001000100010011000110011001000100000000000000000100110010000001001001000000001000100010001101000010001000100010000000000000000010010101001111100010100000000110010001000010100001000100010001100000000000000000110011000100010001010001000011001000100011010000100010001000100000000000000000011001100010001000110000110001000100010001001000010001000100010000000000000000001100110001111100001000001111000010000111000100001000100010001000000000000000000000000000000000000000000000000000000000000000000000000000000010000000000000000000000000000000000000000000000000000000000000000000000000000110000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000After a while, I realized it looked very much like ASCII art. So I tried to extract a flag from it.
And finally:
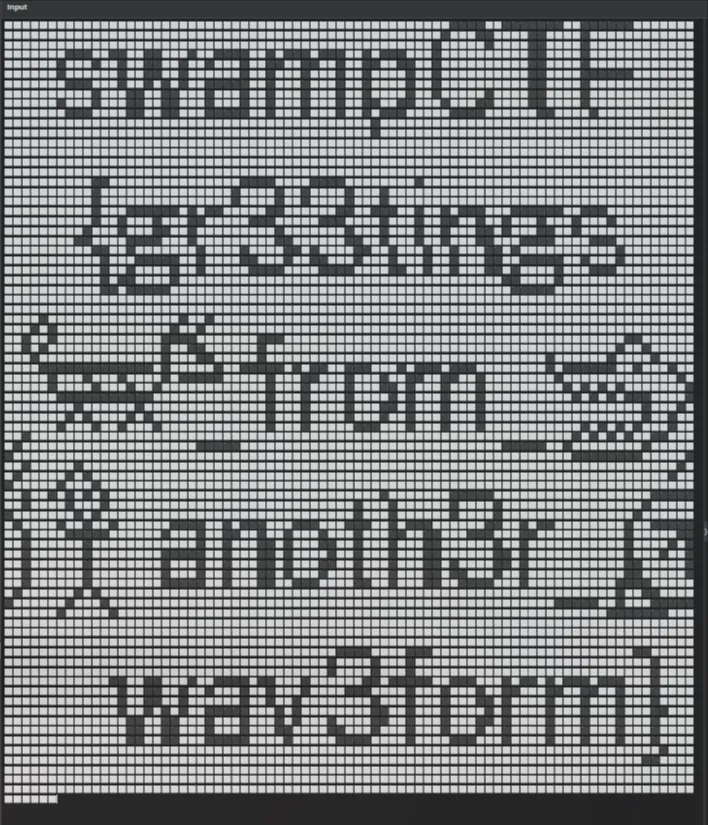
(I converted the 0s and 1s into white and black square emojis to better visualize the whole thing)
swampCTF{gr33tings_from_anoth3r_wav3form}
Blue
The SwampCTF team is trying to move our infrastructure to the cloud. For now, we’ve made a storage account called
_swampctf_on Azure. Can you test our security by looking for a flag?Misc, 79 Solves, 209 points
The description mentions cloud storage on Microsoft Azure that is improperly secured. That immediately made me think of Azure “Blobs,” which are similar to “Buckets” on Amazon (AWS), allowing file storage. These can be misconfigured, thereby exposing information publicly.
There are websites like Public Buckets by Grayhatwarfare that let you search among the “buckets” of major cloud providers, including AWS. Unfortunately, I found nothing there this time. Nor on similar services.
Since Azure blobs follow this format: <storage name>.blob.core.windows.net, I concluded ours must be swampctf.blob.core.windows.net. There was no 404 error.
We can now enumerate/fuzz this URL, and there are tools for that like: https://github.com/initstring/cloud_enum.
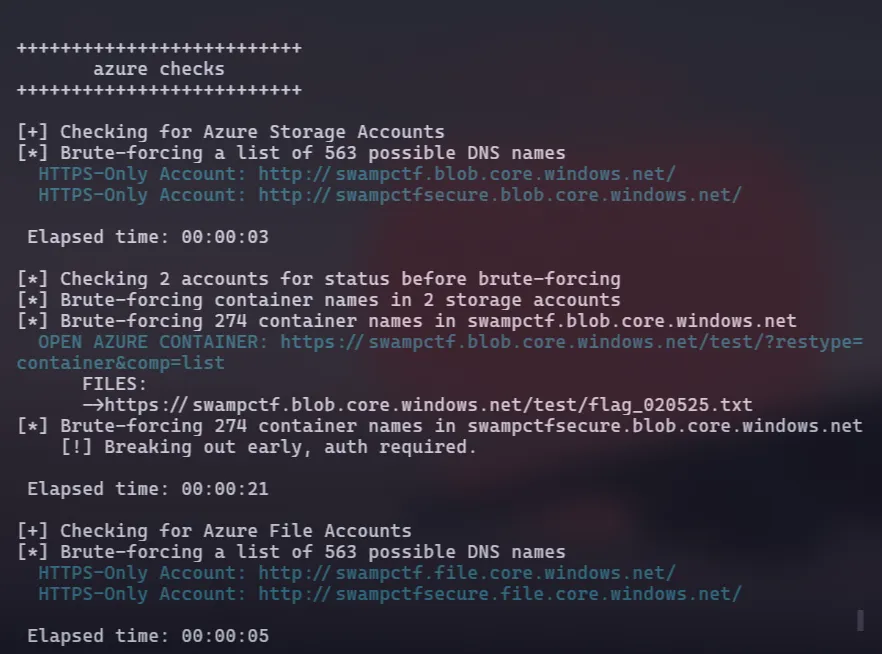
We immediately get some results:
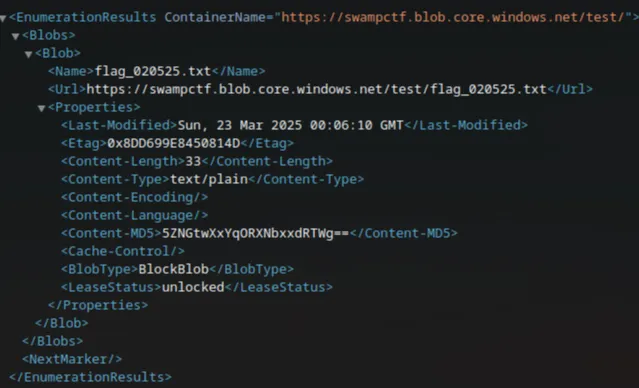
We then discover that the flag was located at this URL: https://swampctf.blob.core.windows.net/test/flag_020525.txt
Flag: swampCTF{345y_4zur3_bl0b_020525}
Pretty Picture : Double Exposure
Hidden in the bits below, an image wait’s to be shown.
Misc, 403 solves, 25 points

We were given an image. Given the title and the image itself, I leaned towards steganography and uploaded it to https://www.aperisolve.com/.

MuddyWater
We caught a threat actor, called MuddyWater, bruteforcing a login for our Domain Controller. We have a packet capture of the intrustion. Can you figure out which account they logged in to and what the password is? Flag format is
_swampCTF{<username>:<password>}_Forensics, 141 solves, 200 points
We were given a .pcap file with a large number of requests. Observing the packets, we quickly noticed the brute force targeted the Domain Controller via SMB2 protocol. The goal was to find when the DC login succeeded. Not knowing exactly what message signaled a successful authentication, I sorted the packets by size to spot anything out of the ordinary.
A Session Setup Response with an unusual size (139 bytes) is often associated with a successful authentication.
We can easily find the user involved, hackbackzip. Now we just need to extract their password. To do this, we reconstruct the NTLMv2 response, which has this structure: USERNAME::DOMAIN:ServerChallenge:proofstring:blob
We’ll use Wireshark to manually extract everything.
Here we have the NTLM Server Challenge.
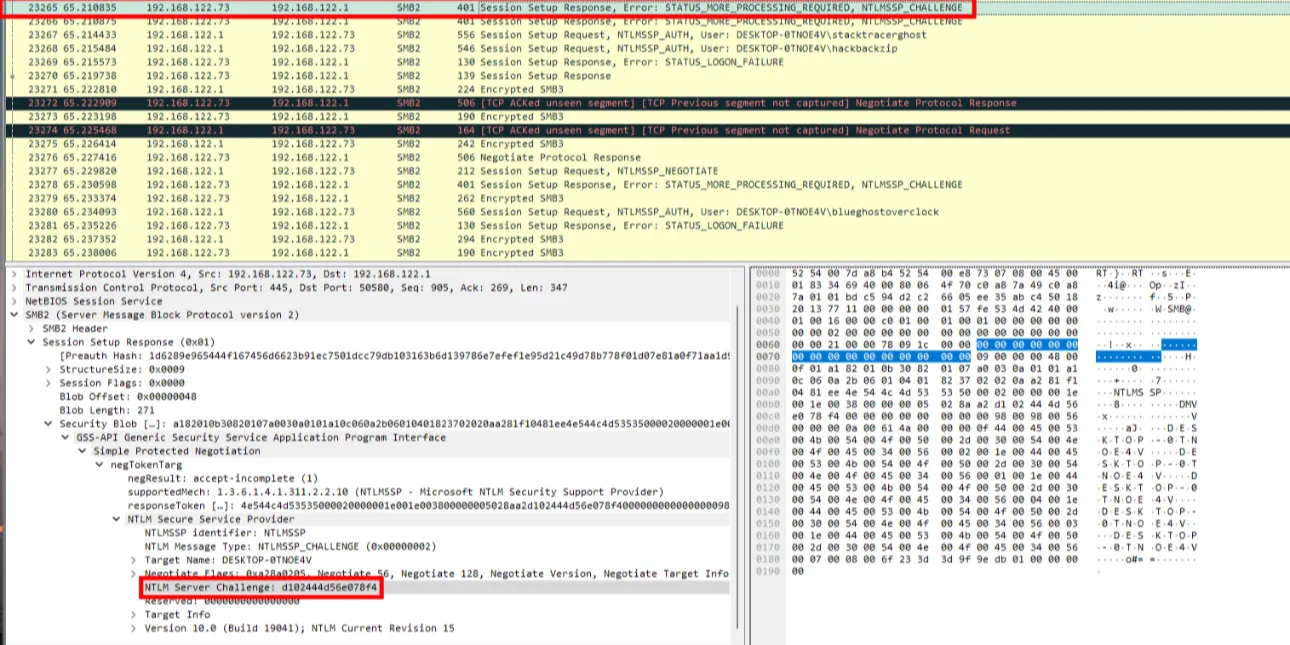
Next, we can find the NTLMv2 response, as well as the username and hostname to reconstruct the NTLMv2 response. We extract the NTLMv2 response from the SMB packet: it consists of the proofstring (first 16 bytes, or 32 hex characters) and the blob (the rest). We separate these two for Hashcat’s mode 5600.
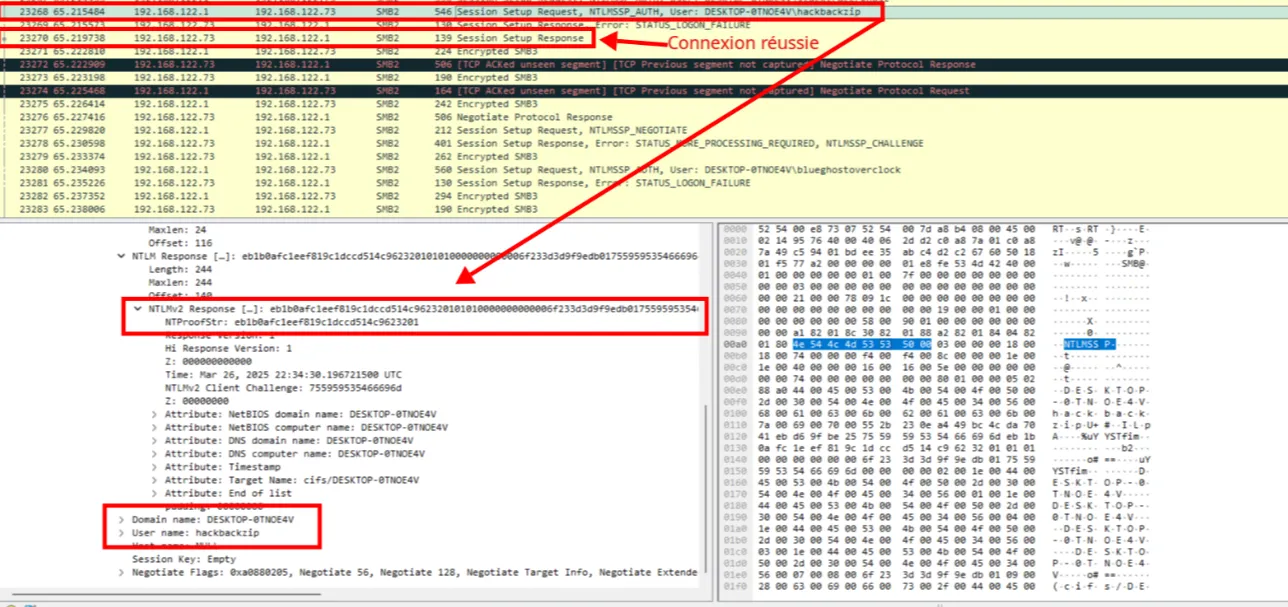
Here is the complete NTLMv2 response:
hackbackzip::DESKTOP-0TNOE4V:d102444d56e078f4:eb1b0afc1eef819c1dccd514c9623201:01010000000000006f233d3d9f9edb01755959535466696d0000000002001e004400450053004b0054004f0050002d00300054004e004f0045003400560001001e004400450053004b0054004f0050002d00300054004e004f0045003400560004001e004400450053004b0054004f0050002d00300054004e004f0045003400560003001e004400450053004b0054004f0050002d00300054004e004f00450034005600070008006f233d3d9f9edb010900280063006900660073002f004400450053004b0054004f0050002d00300054004e004f004500340056000000000000000000**hackbackzip**→ Username used for authentication**DESKTOP-0TNOE4V**→ Hostname**d102444d56e078f4**→ServerChallenge, an 8-byte random challenge sent by the server**eb1b0afc1eef819c1dccd514c9623201**→proofstring, an HMAC-MD5 derived from the NTLM hashed password**01010000000000...**→blob, containing metadata such as timestamp, client challenge, and target info
Now that we have the full NTLMv2 response, we can use Hashcat (a tool for brute-forcing hashes and more).
Command: hashcat -m 5600 -a 0 ntlmv2_hashes.txt /usr/share/wordlists/rockyou.txt
Mode 5600 is for NTLMv2, we use rockyou.txt, and specify a dictionary attack with -a 0.
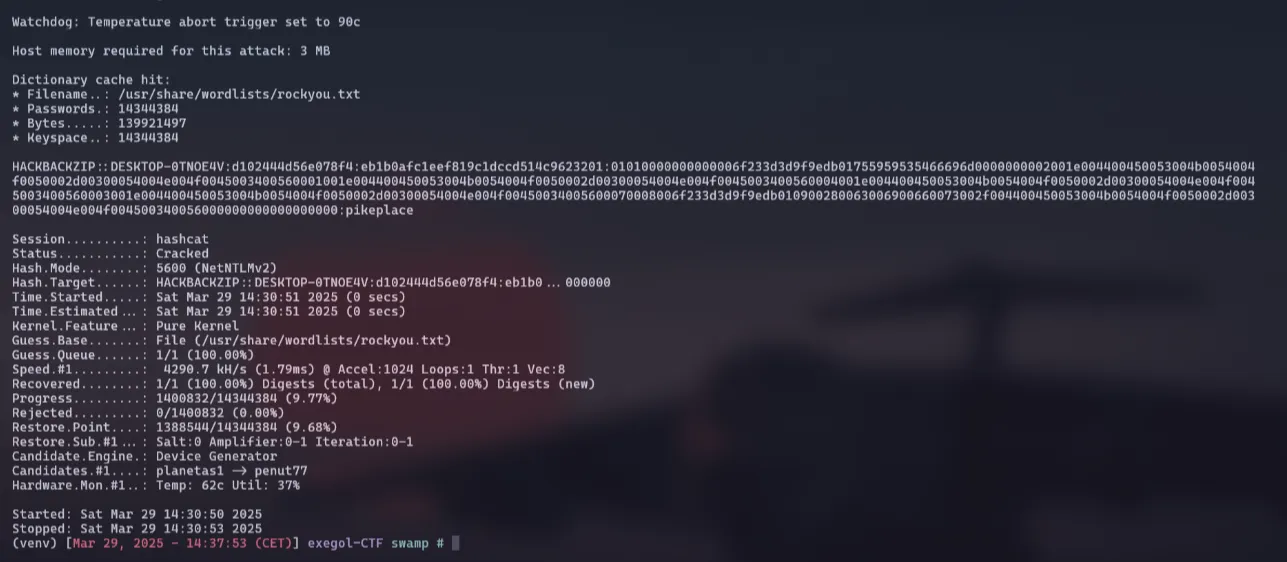
We then get the password pikeplace, which gives us the flag:
Flag: swampCTF{hackbackzip:pikeplace}
Resources:
https://www.youtube.com/watch?v=mu7-naA0muc
https://hashcat.net/wiki/doku.php?id=example_hashes
Party time ! Level 2
The party just ended, but people are hungry. Find the nearest fast food spot to see where everyone went!
The flag format is swampCTF{…}. You will not need to wrap it yourself.
OSINT, 183 solves, 150 points
Given the coordinates from the previous challenge, we had to find the nearest fast food restaurant. I like using Overpass Turbo for this kind of task; I wrote a short query to show fast food-related points.
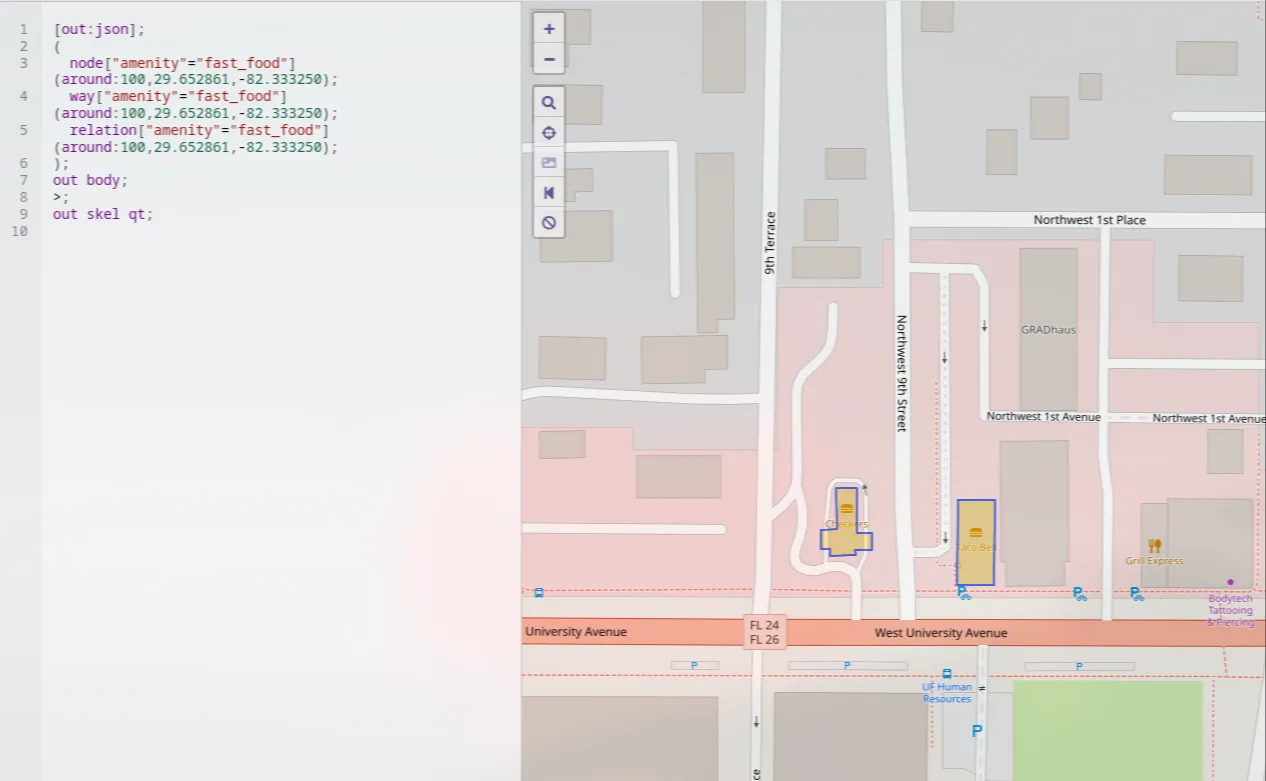
We found two very close spots. I decided to check the reviews first, since that’s the best place to hide a flag, and I sorted them by publication date.

And there it is!
On Thin Ice
I’ve been looking for well-rated ice-skating rinks, I wonder if there is one out there with decent reviews?
The flag format is swampCTF{…}. You will not need to wrap it yourself.
OSINT, 87 solves, ? points
For this challenge, we were given an image that appeared blank, but with hexadecimal in the EXIF data:
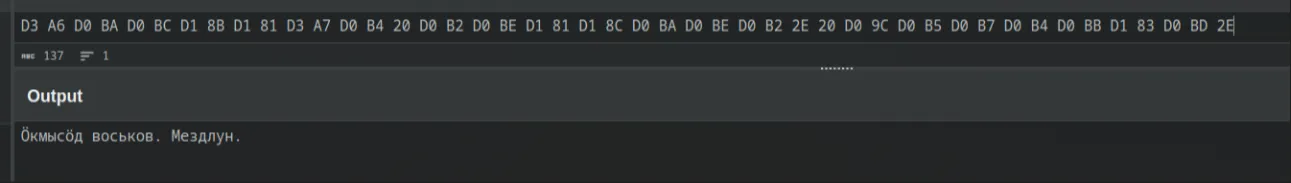
I quickly identified that it wasn’t Russian, but a local language from the Komi people in northern Russia.
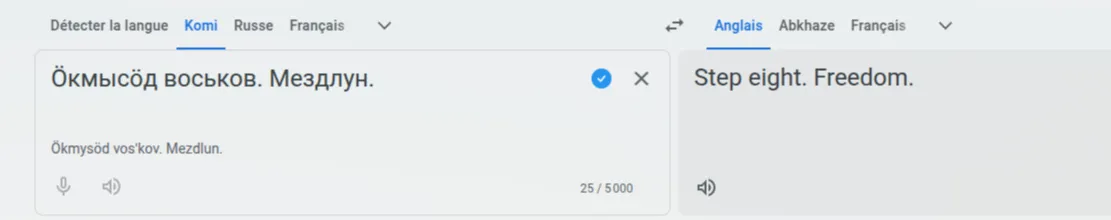
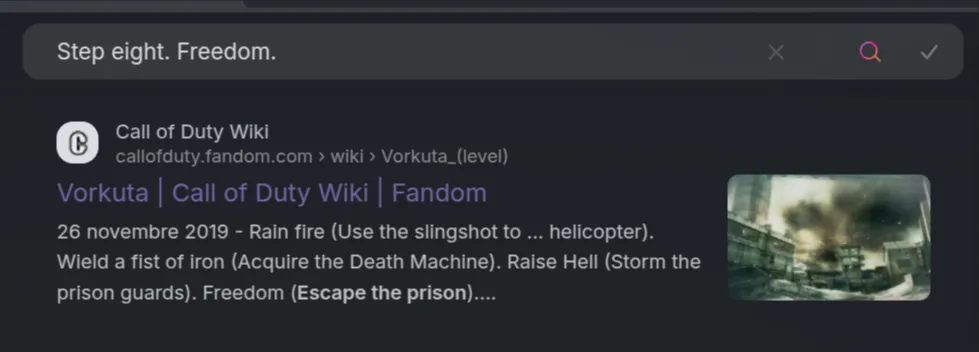
Interesting. Since it didn’t ring a bell, I simply searched online, and one article stood out—“Vorkuta,” a fairly well-known city in northwestern Russia.
Since our goal was to find an ice rink, this time I used Google Maps instead of bothering with Overpass Turbo queries. And like in the previous challenge, I looked through the Google reviews of each result, filtering by the most recent reviews.
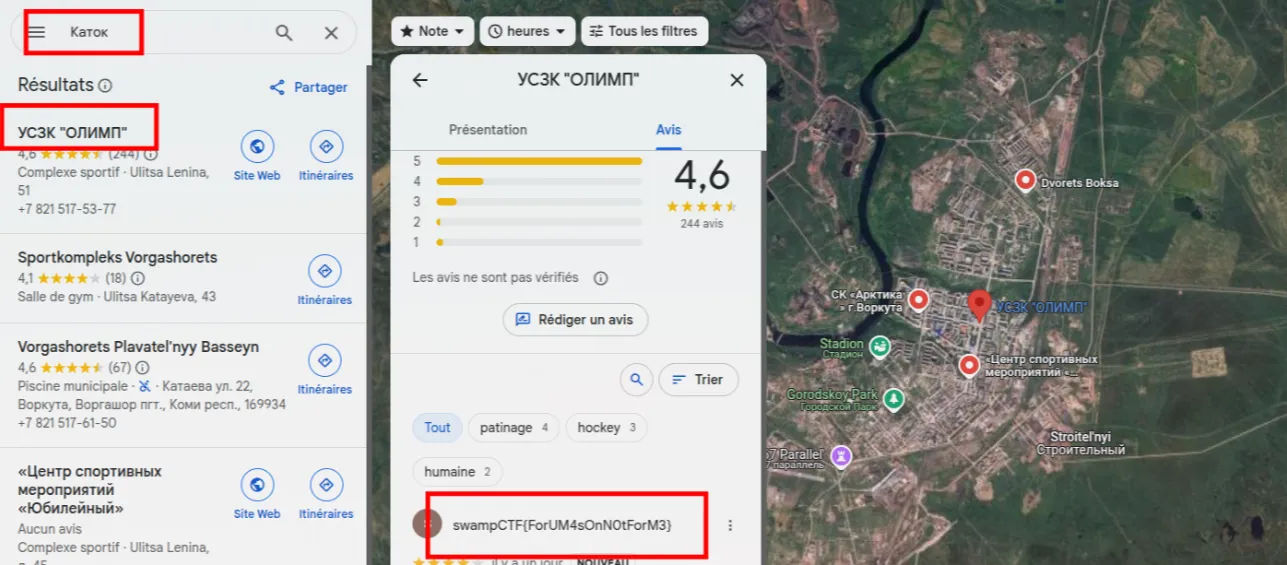
swampCTF{ForUM4sOnN0tForM3}