Hack'OSINT 2025

Introduction
We tackled it as a duo and finished 8th out of 170 teams that solved at least one challenge—only 9 of those teams completed the full investigation over the weekend. I’m going to be deliberately exhaustive so that even people with very little OSINT experience can follow along.
This CTF was 100 % OSINT. It followed on from HACKOSINT 2024, which told the story of an investigation into Chloé, who fell victim to a phishing scam and lost €10,000. With help from her friend and last year’s investigators she traced the attack back to the hacker group APT‑509, which turned out to be a well‑oiled criminal organisation. That first investigation led to the arrest of several members; now it’s time to deal with the ones who slipped through…
The challenges are presented in the order we received them. At the start of the CTF we were given a document describing the situation outlined above.
Interview
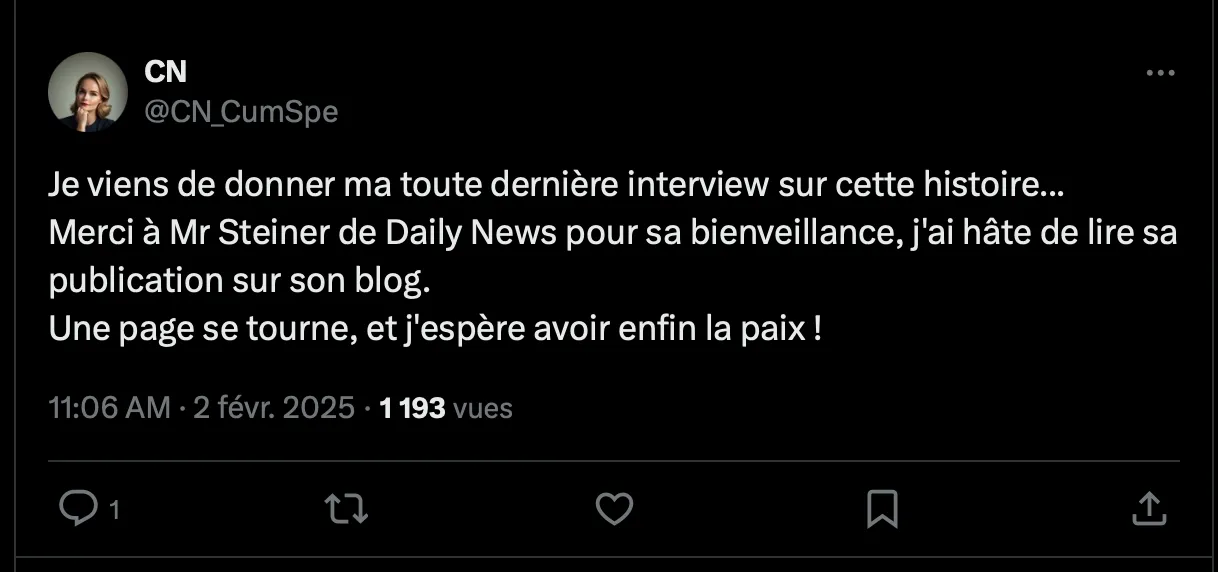
The previous document shows that the interview given by Charlotte is a good starting point. Can you find the exact date on which this interview was conducted?
In the PDF you can find Chloé’s X (Twitter) account. On it there’s a post dated 2 February saying she did the interview with Mr Steiner from Daily News.
Who are you?
In this interview, Charlotte mentions the name of someone who behaved suspiciously toward her. Could you tell us that person’s full name?
Flag format:Victor Hugo
Still on Chloé’s X account we find this post with a discreet caption:
We suspect we’re looking for a Medium article. A quick dork later and we land on these posts:

On the author’s Medium we find several articles, including the interview with Chloé. Here’s the relevant excerpt:
Username
This Nicolas is very active on social media. Can you find out what handle he hides behind?
He has a Facebook account:
https://www.facebook.com/profile.php?id=61576075067801
One post grabs our attention:
His T‑shirt has the username on it.
First contact
While digging into this username, you discover a place full of secrets that should have remained confidential. Can you determine exactly since when Nicolas has been chatting with Foxtrot (former APT‑509 member arrested in 2024)?
Nothing too hard yet (that will come soon enough). We use our favourite tools—personally I’m fond of RhinoUserChecker and whatsmyname.app.
A quick RhinoUserChecker run and bingo:
https://bsky.app/profile/xnicolasht.bsky.social
A post with a photo immediately catches the eye:
We’re looking for a .fr drive site… CryptPad!
Just type the address
https://cryptpad.fr/drive/#/2/drive/view/f3YGBpPsdLVDxwpvH+PfWsHBS2nNHpOgLwGr-VP9cHI/
From the initial PDF we know Foxtrot’s real name is Hugo Lecompte. Browsing the directory we come across these screenshots:
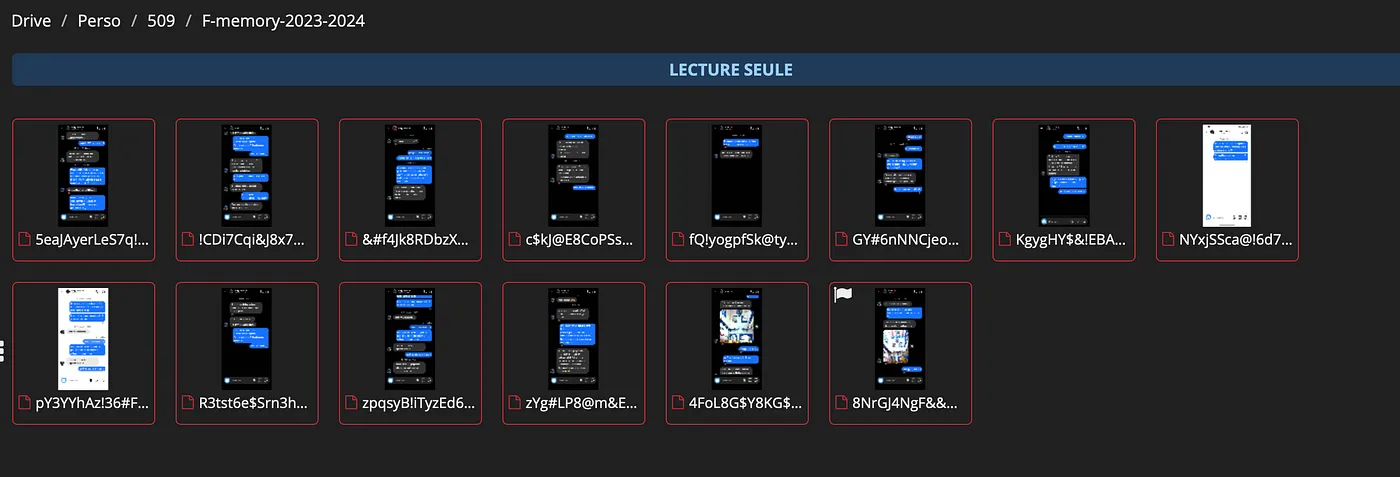
And that’s the flag: 07/09/2023.
Knock knock knock
With the information you have, can you pinpoint Nicolas’s exact home address?
Well well, probably the most stubborn challenge of the whole CTF—I spent the entire weekend on it. For comparison, here’s the message traffic difference between earlier channels and this one:
I don’t have exact stats but I think this blocked most teams; we finally flagged it one hour before the end.
So, what do we have?
We’re looking for a house in the Ain département (already helpful). But that’s not our only clue. We deduce that there was no traffic in his street the week before 17 February 2024, and that traffic resumed between 17 February and the following summer. Nice leg‑up…
We also know his house is under renovation on Street View. Lovely leg‑up indeed…
Here’s where I made my first big mistake, one that haunted us for ages… I figured that since we had no other info, it must be an obvious city: Bourg‑en‑Bresse, the capital of Ain. Then I looked at his Facebook profile where this pops up:
Bingo!
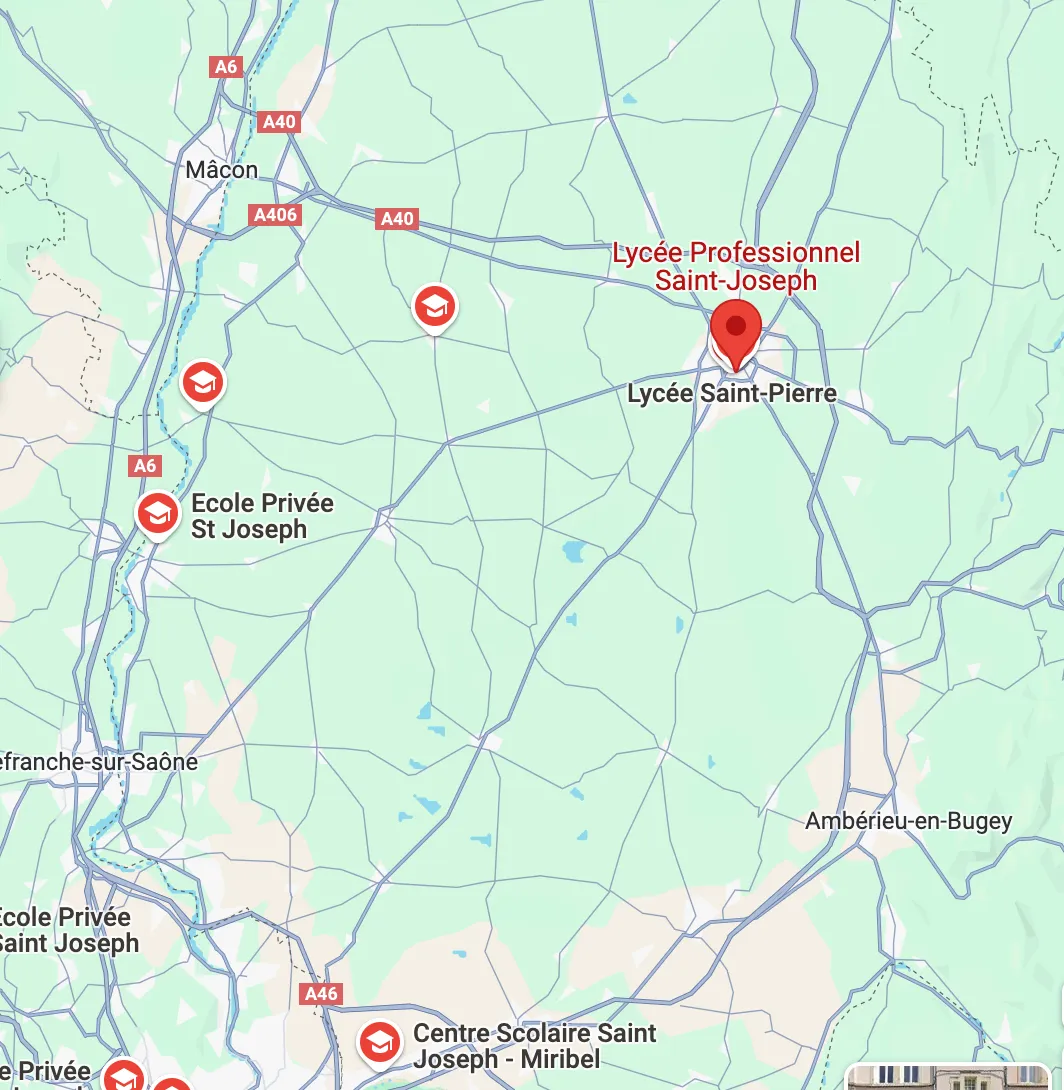
There’s a Lycée Saint‑Joseph in Bourg‑en‑Bresse. Narrowing the search, we’re sure to find the house soon—it’s only challenge 5, can’t be that hard, right? ^^
^^
I spent hours on this with nothing solid. To keep this write‑up from ballooning to 500 pages: after combing through dozens of official documents, road‑work notices, every possible phrase for “road closed”, “blocked street”, “construction”… and what if it’s not a rue but a chemin, passage, avenue?
Nothing.
After overheating Google with increasingly far‑fetched dorks, I took the hint Sunday morning (the challenge unlocked Friday night):
All right, no more dorks; focus on Bourg‑en‑Bresse city hall. Still no luck, and after losing years of life expectancy and a few hundred hairs I accepted that we needed another town… Initially Bourg‑en‑Bresse was just a hunch. Seeing a Lycée Saint‑Joseph triggered massive confirmation bias—I convinced myself it had to be Bourg‑en‑Bresse, costing lots of time. Plus I was mostly alone on this challenge.
Anyway, other towns also have Saint‑Joseph schools; after more digging we zeroed in on two possibilities: Miribel and Oyonnax. Of course there’s nothing on their municipal sites because the works are over a year old. Dang! Time to go back in time! Enter the Wayback Machine.
Oyonnax: apart from the news section, nothing on urbanism… Miribel: there’s a “Current Works” page that lets you download a PDF listing road‑works for the next three weeks. Perfect! Small problem: on Wayback the first snapshot is 22 Feb 2024, i.e. after our target date.
Let’s still check every “road closed”. Nothing. So it’s Miribel after all? Yes.
Consider the link
https://www.miribel.fr/wp-content/uploads/2024/02/Planning-des-arretes-en-cours-2024-Semaines-n%C2%B08-a-11.pdf
Hmm… Could we tweak the URL to reach the file we want even if it’s not linked anywhere? We have weeks 8‑11; logically we’d also have 4‑7 and 1‑3. Let’s try!
Oops!
Surprisingly, week 4 of 2024 was in January! Maybe the /02/ in the URL is the month folder? Let’s swap 02 for 01.
Bingo!
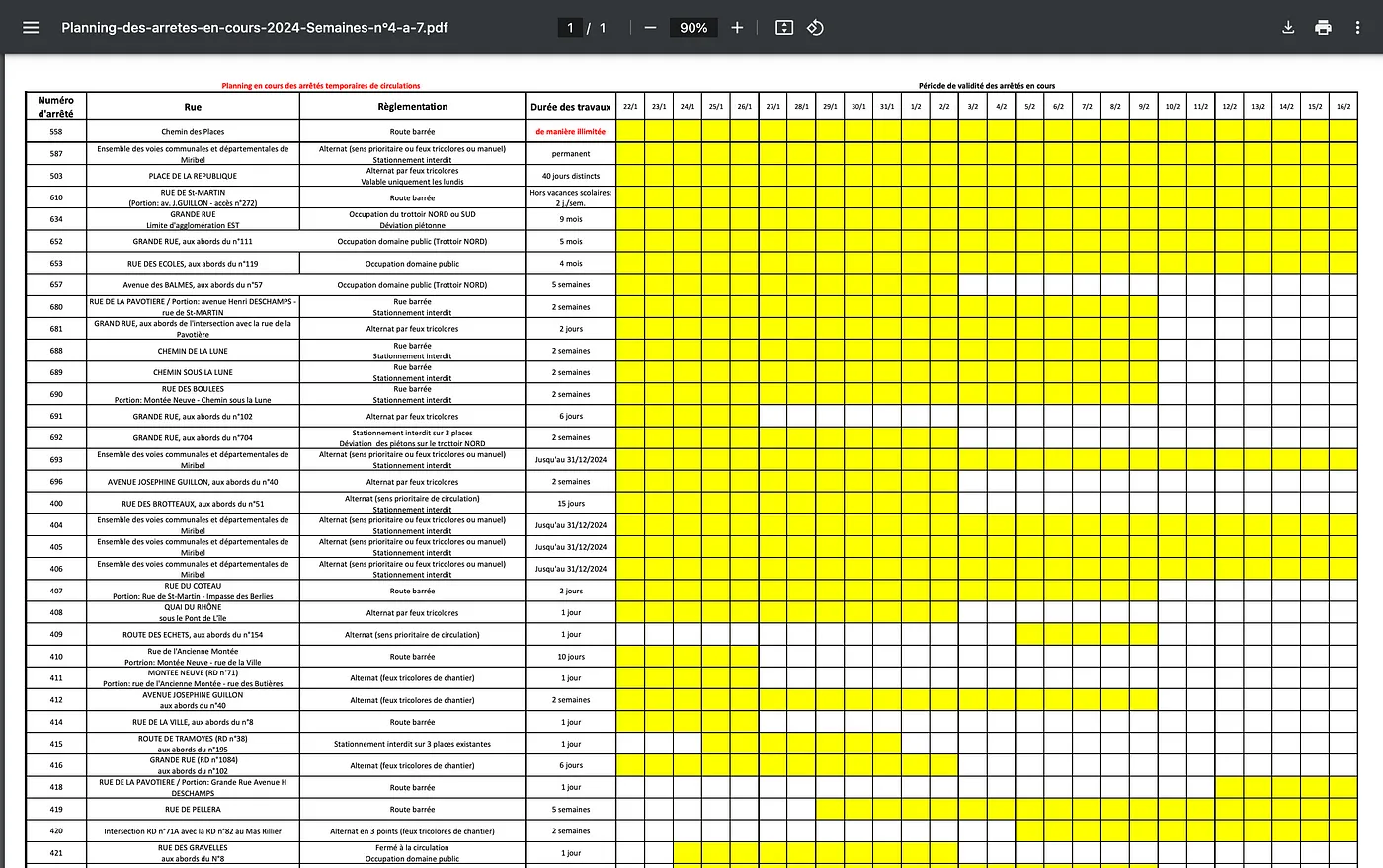
Now try each “road closed”. And there’s the house:
Submit—and it’s a flag!
Holidays with friends
While analysing the chat between Nicolas and Foxtrot (Hugo Lecomte), one conversation stands out. Can you find where Foxtrot went on holiday last year and the flight number of his outbound trip?
Flag format:Paris J1 2345
On the CryptPad we have:
Google Lens on the photo returns
https://www.instagram.com/reel/C7XIBUtt_WQ/
So it’s a restaurant in Marrakech.
We look for a Roissy‑Marrakech flight:
On the 11th at around 7 a.m. Using Flightera we list flights at that time:
https://www.flightera.net/route/LFPG/GMMX/2025-05-10%2005_20
Flag: U246663
Identity
While investigating Foxtrot and Hotel’s trip to Marrakech, can you find Hotel’s real identity (first and last name)?
On TripAdvisor, in the restaurant they visited, search the reviews for “Hugo”:
https://www.tripadvisor.fr/Profile/78478HBethune
The first name is on the page and the surname in the URL.
Flag: Henry Bethune
A lucky one
Henry seems to have slipped through the net during the first inquiry in 2024. Can you tell where he was at the time of the initial APT arrests?
The arrests were in June 2024 according to the PDF.
From the earlier article we have:
We find a Bluesky account with the same handle as on TripAdvisor. There’s a post describing a trip in that period:
On the 23rd we have this ticket:
It’s this restaurant in Asakusa, Tokyo.
That’s the flag.
Double identity
Henry Bethune appears to come from another country. Can you find his second identity and give it to us in the linguistically correct form for his native language?
Flag format:Jérome Lévêque
On his Bluesky one picture attracts attention:
Flag: 佐藤 蓮 (Ren Satō)
Where are you?
Can you determine Hotel’s current location?
Flag format:Parc de l’Auxois
RhinoUserChecker reveals his Snapchat:
https://www.snapchat.com/add/henrybtravel
We saw photos of Disneyland Paris, but not the main park.
With a bit more digging we land on this article:
https://allears.net/2023/05/22/re-imagined-walt-disney-studios-park-still-has-a-way-to-go/
Flag: Walt Disney Studios Park
Reveal your secret
Hotel seems to be in contact with another person. It would be useful to investigate her! Can you find her full identity (first and last name)?
From the earlier screen we get the handle @lg‑account.
In one of her stories there’s a dog tag with a phone number:
The number leads to this site:
During the challenge, an emoji indicates some interaction is needed. Subscribing to the newsletter returns an email with questions; answers are hidden in EXIF data or the source code.
Flag: Léa Gaudreau
How many winters?
Age always matters, especially for determining legal sanctions. How old is Léa Gaudreau?
Her Instagram: https://www.instagram.com/lgaudreau_/
Her bio says she is 27.
CCTV
With the information you have, can you identify a very specific shop that November visited? That would let us obtain CCTV footage (even old) and learn more about her and possibly her associates.
On her Instagram she’s clearly an Apple fan. We also find her professional email: lea.gaudreau.pro@gmail.com
Using Epios we find her Google Calendar:
https://calendar.google.com/calendar/u/0/embed?src=lea.gaudreau.pro@gmail.com
Two entries interest us:
Now we just need an Apple Store in Lyon’s 3rd arrondissement. There’s only Apple Lyon Part‑Dieu.
Hotel California?
November doesn’t seem to have a fixed address. Can you determine exactly which flat she currently lives in?
Her Instagram points to Threads: https://www.threads.com/@lgaudreau_
First clue we see:
An Eiffel‑Tower‑view Airbnb whose host is called Nicolas. A dork yields tons of results—we still need one more piece.
This post grabs us:
We look for her Vinted, eBay, Etsy, Leboncoin—start with Vinted. Bingo: https://www.vinted.fr/member/266597511
From here we recover the Airbnb listing:
https://www.airbnb.fr/rooms/53885435
I used Google Earth (street‑level Google Maps was too hard).
Key features: the rounded roof next to a flat roof with chimneys and a blank wall behind.
To confirm, Street View for matching railings:
Bingo—flagged.
The girlfriends
From what you found about November, she seems to be dating an APT‑509 member. Can you identify that person’s full name?
A Threads post gives us:
RhinoUserChecker on JLMaigot: https://www.chess.com/member/JLMaigot
She plays frequently with m8_saunier:
https://www.chess.com/member/chessm8_saunier
RhinoUser again on that handle yields a Linktree:
https://linktr.ee/m8_lsaunier
Which leads here (useful later):
https://mymemoriegram.xyz
We know the surname Saunier; only the first name remains. Another Threads hint:
Lise Saunier => flag!
Happy Birthday!
To complete our investigation file, could you provide Bravo’s full date of birth and her birth département? With that we can check whether she’s involved in other cases.
From the previous link we have:
Scanning the barcode:
It’s a French social‑security number! She was born in 1993 in département 84 (Vaucluse). In her girlfriend’s calendar: L’s birthday on 14/08. Flag: 14/08/1993 Vaucluse
The key element
Analysing the info on Bravo, a conversation mentions an app that looks intriguing. What is the ID of this app?
Check https://mymemoriegram.xyz/robots.txt
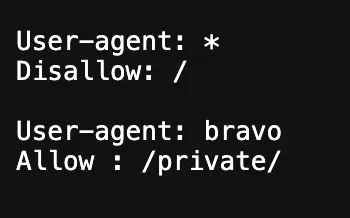
Go to https://mymemoriegram.xyz/private/ with the User‑Agent set to bravo. Lots of documents appear.
One message stands out:

Quick search in the Google Play Store reveals:

Flag: com.hackosint.myapplication
The hidden message
What a strange app! Once launched it seems to be a front hiding APT‑509’s cyber‑criminal activities. One of our experts inspected the source and suspected an email address is hidden inside but couldn’t locate it.
Inside the app there’s a chat:
Switching the app to dark mode reveals the email:
Flag: str3etf1sher@mail.com
Communication
APT‑509 also seems to use another communication channel alongside the app. Can you specify the creation date of that channel?
Following the Telegram in the previous convo:
Flag: 25/04/2024
Fly away
On this drive you find a drone video by Alpha scouting a new bunker location. Can you identify the drone’s take‑off point?
Telegram gives us this CryptPad:
We unlock it with the password from Lise’s drive:
Here’s the video snapshot with landmarks:
We find the spot:
Take‑off point:
Flag!
New target 2
After the 2024 arrests, APT‑509’s activity is declining. Their planned attack on Geelong, Australia failed, hurting their funds. To relaunch, they plan a cyber‑attack on a French company. Which one?
On CryptPad we find:
Remove the watermark and we get:
Clearly a decent‑sized train station. Top of the image shows:
I open Google Earth and scan big eastern‑French stations until I land on Reims:
It’s the CIC bank branch:
D‑Day
Can you determine the date of this planned cyber‑attack?
We find this on CryptPad:
Remove the noise, left with:
Flag: 17/07/2025
Username 2
It appears GOLF is monitoring our chats and French OSINT news. Can you identify the username of the account he’s currently using to spy on us?
Back to Telegram:
Screenshot shows the handle g0lf_et_apt.
Sorry, you are?
That app hides big secrets! The email address seems a good lead to track Mike.
Can you give Mike’s full identity (first and last name)?
Using str3etf1sher@mail.com we find this Mastodon account:
https://mastodon.social/@str3etf1sher
F Daucourt—now we need his first name. Recall this image:
It mentions a fishing trip with a Fabien. Flag: Fabien Daucourt
Little boat
Mike is an avid fisherman and well equipped! Can you find the MMSI identifier of his boat?
First, what’s MMSI?
The MMSI is a nine‑digit code assigned by ANFR to vessels with radios using Digital Selective Calling.
We find F Daucourt on a fishing forum:
https://absolu-peche.fr/profil/10018-f-daucourt
Profile blurb:
Tight lines or full throttle: I live for fishing and cars. The calm of water, the roar of the road.
⛵ Seashell Injection
On MarineTraffic:
https://www.marinetraffic.com/en/ais/details/ships/shipid:9565794/mmsi:912010044/…
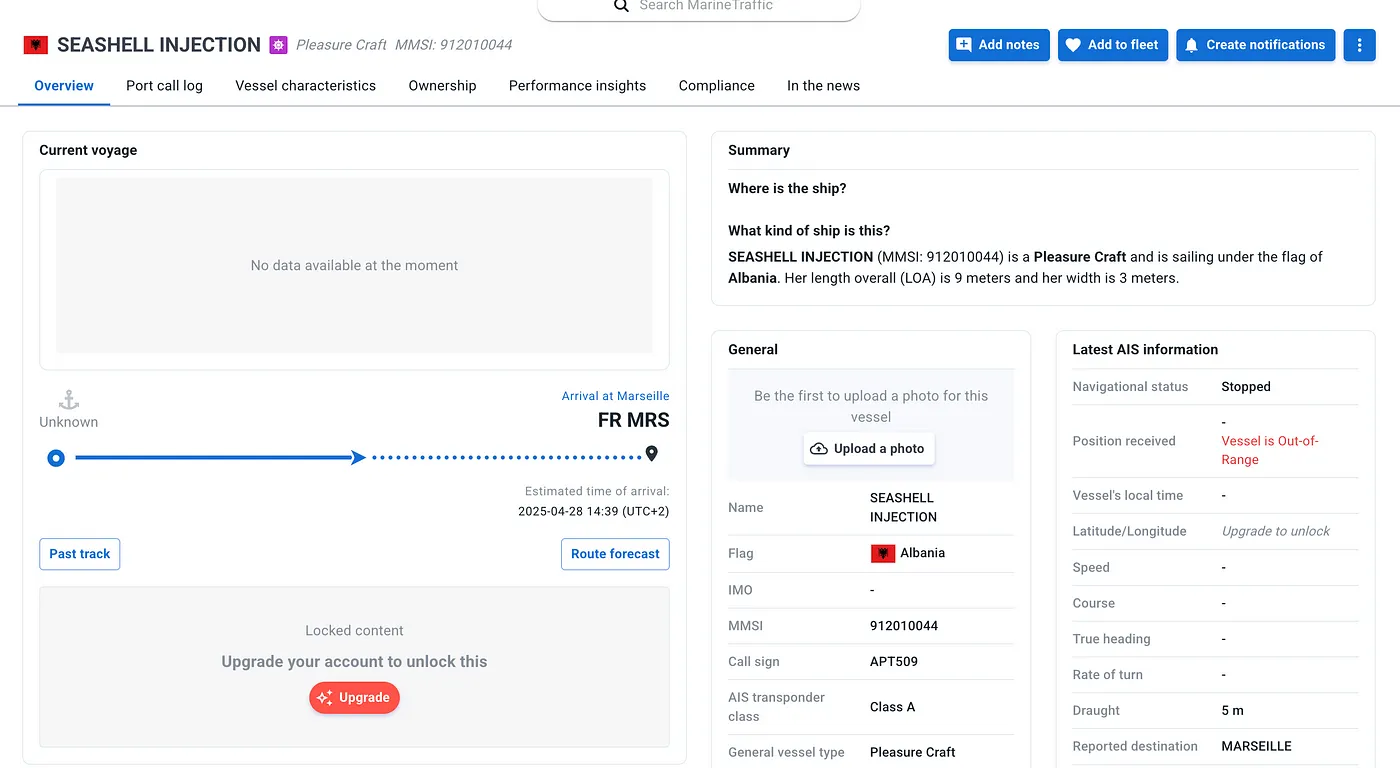
Call sign APT509—our boat!
Home sweet home
Based on what you have, can you name the village where Mike lives?
On the forum Mike posted:
We need Lake Saint‑Agnan on Google Maps:
Spot the D211 at bottom‑left; follow it to the D6:
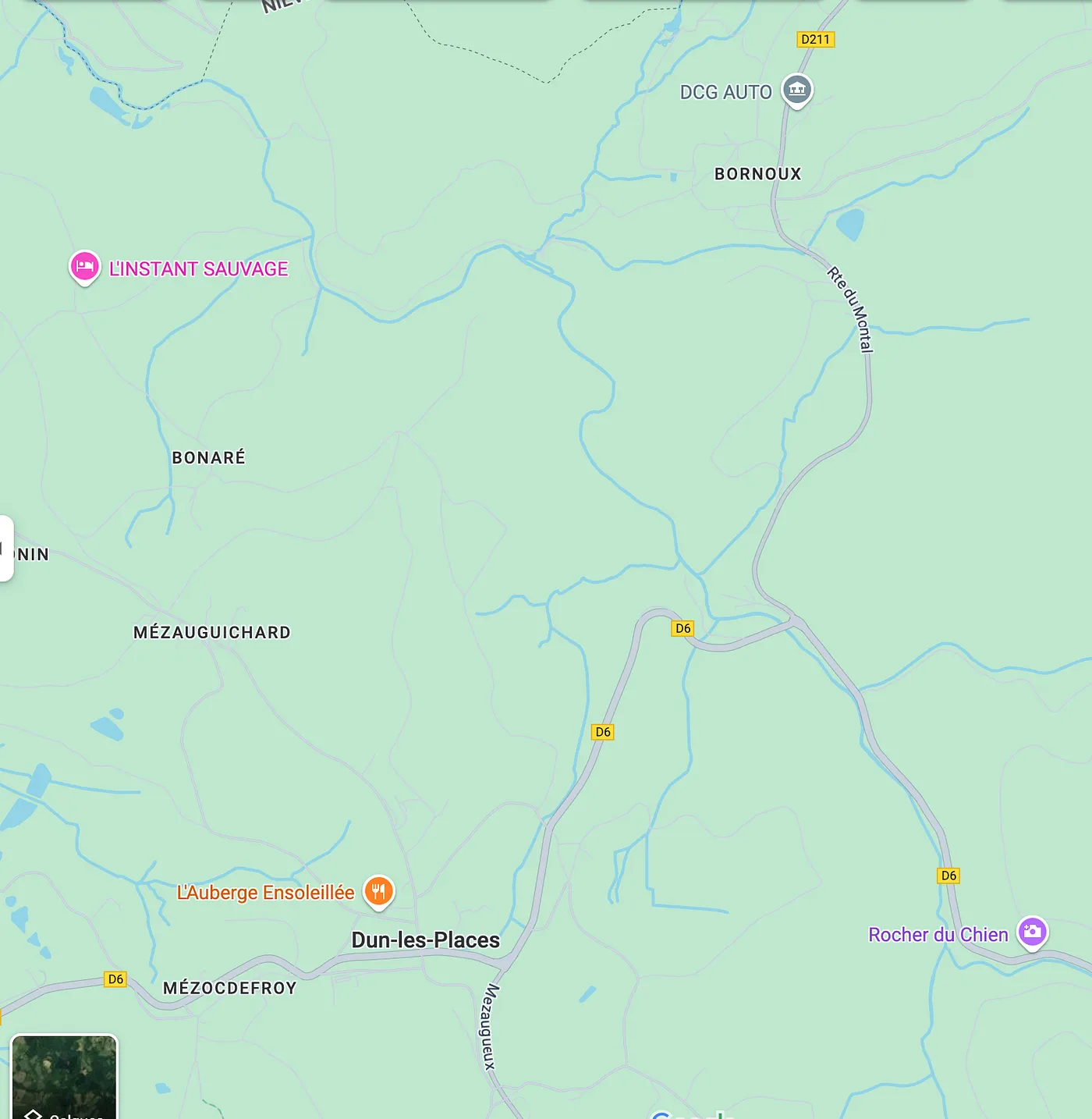
Flag: Dun‑les‑Places
Objective EAGLE
This area is popular with drone pilots. Can you identify the exact model Alpha used? Useful if we detain him.
In CryptPad there’s a .txt log:
https://cryptpad.fr/drive/#/2/drive/edit/l2MS2EEV9OuI0mEnOo2rW7Xw/p/
It’s a DJI log:
Flag (drone model).
A strange company
They’ve begun buying supplies for the new bunker. APT‑509, now famous, can’t buy under their real identity without risk. Under what fake name do they purchase gear?
CryptPad contains an invoice. No company visible—until the EXIF:
Flag: betaoespatulaparker
Back to Mike…
Showcase site 1
Judging by APT‑509’s methods, this fishing story is more complex… leading somewhere else. Which site does the boat point us to?
In the vessel details earlier we saw:
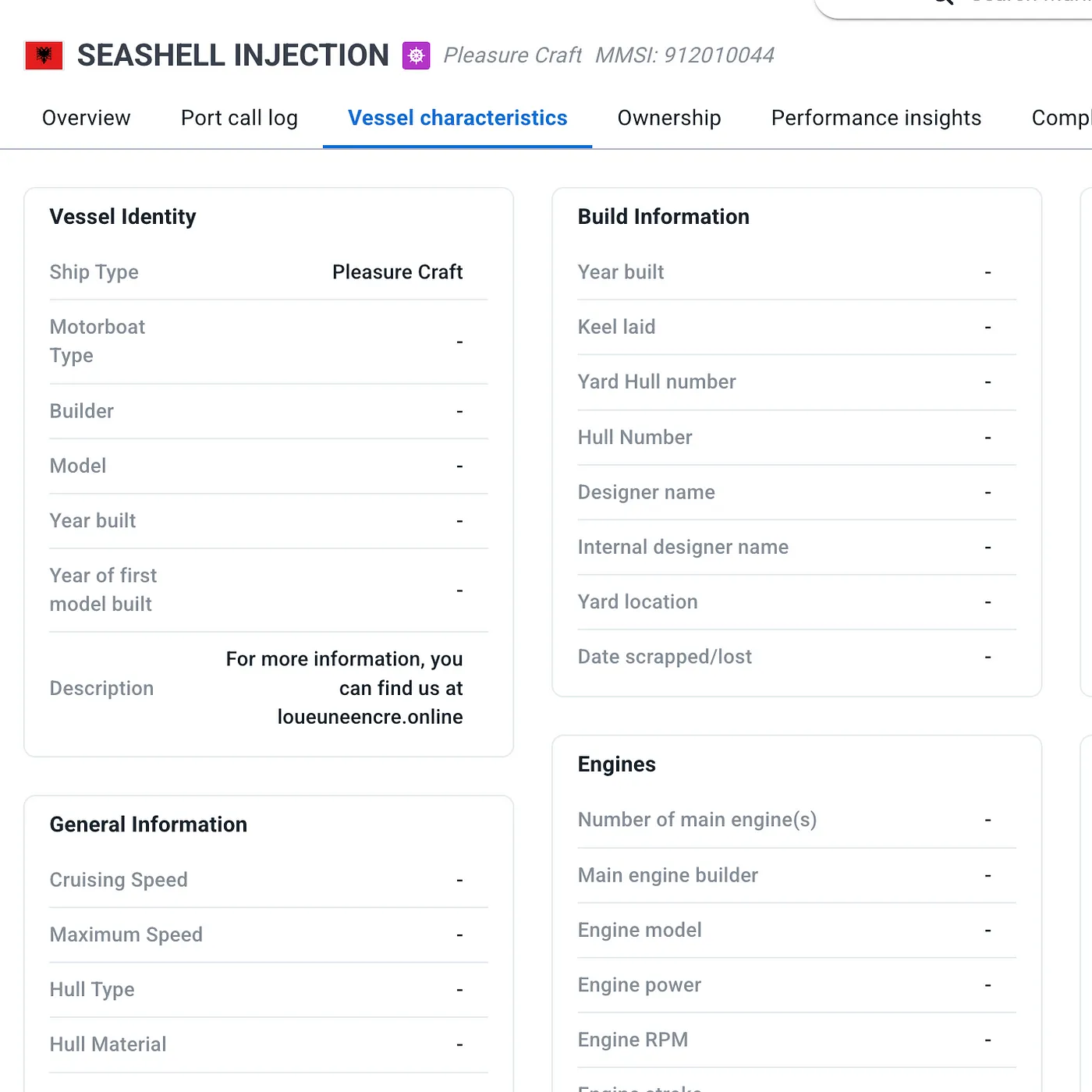
Flag: loueruneencre.online
Showcase site 2
Like any (even fake) company, it probably has a showcase website. Can you find its address?
We find: https://betaoespatulaparker.eu/
Needs a Portuguese VPN to access.
Flag: betaoespatulaparker.eu
The ally
While exploring the boat‑rental site, it seems an allied investigator is also digging into APT‑509. He infiltrated their hidden dashboard and extracted sensitive files, leaving a breadcrumb for anyone wanting to take the group down. Can you identify this investigator’s handle?
On Wayback in the URL tab we notice:
Source code gives login details for the previous link:
We access a hidden dashboard:
Typing “alert” shows:
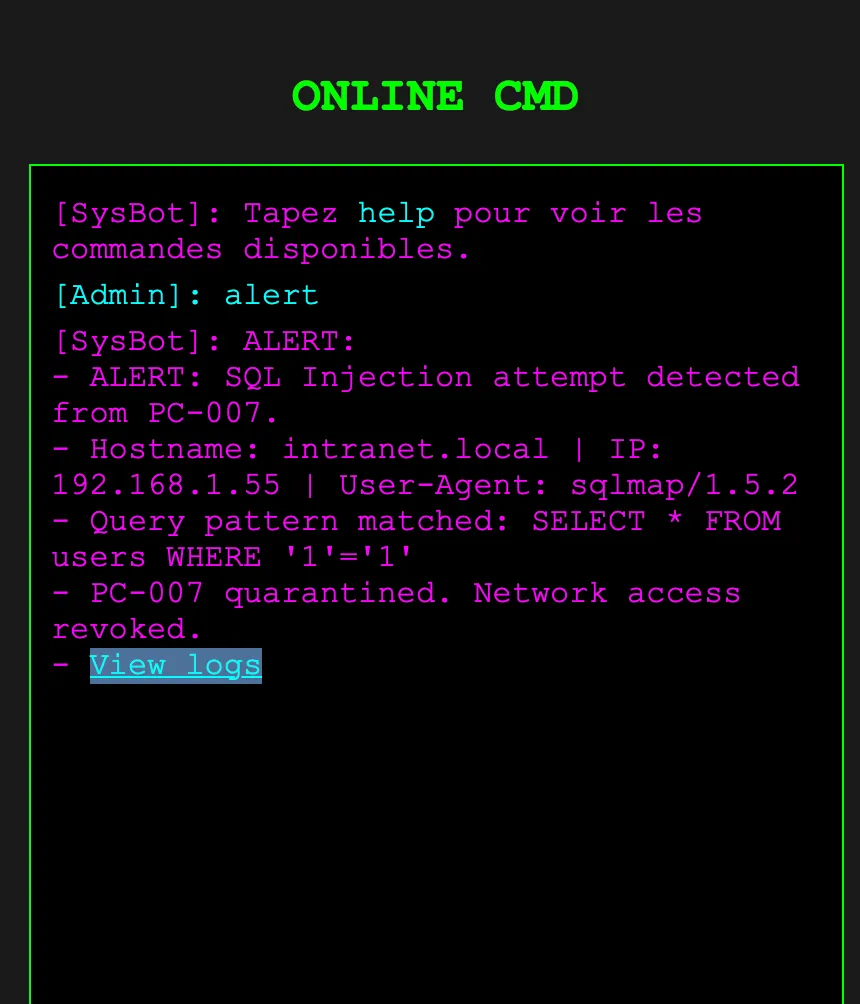
Logs lead to a page containing:

Handle: 3ND0FW47CH509 — flag!
Gold mine
This investigator is a real ally! He managed to leak sensitive APT‑509 files. Our experts found one of his accounts; its description reads:
If you’re here, you too want to end the 509 threat. GL! I’ve left some info about a key character (#A) online. You’ll find it useful!
Can you retrieve that data and, using it, identify another website used by APT‑509?
We actually bypassed the intended path. Thinking about data drops, Pastebin? Search Pastebin for APT‑509:
Inside is base64 that decodes to:
Yields
http://o24pswwbpjzy6hc36mfbxpy6xqayy7cta4w5xfoortwvehb272eeefyd.onion/
The forgotten one
Info on this new site suggests someone was playing a double game… Can you identify their code‑name and role within APT‑509?
On the site we’re “blocked”:
Just remove the #hacker element in source.
A post was deleted. It talks about Kilo, the double agent. We infer it’s Chloé’s “friend”. After trying to fetch files we look for archives:
New recruit — Kilo
Author: Alpha — 07/08/2023
Welcome to Kilo! She joins in ghost mode: she won’t appear on the org chart, that’s deliberate. Her mission? Spot targets, assess how manipulable they are… In short, she’s our “social‑intelligence officer”—everything that isn’t written down. She’ll operate under a fake identity: Ainoa Fernandez. She’ll drop by the bunker next week to introduce herself.
Flag: Kilo – social‑intelligence officer
Stealth guaranteed
This site seems fresh and not fully secured. With what you know, it’s finally time to pay “Alpha” a visit.
We find:
https://betaoespatulaparker.eu/IMPORT-VPS-SITA-ficheiro/
Several docs, one of which:
OBJECTIVE:
On‑site quarterly meeting
MEMBERS:
#A,#G,#N,#B,#H,#M #K?
COMMUNICATION:
T private‑509
SECURITY:
#A secure remote hideout
#G,#N,#B,#H,#M solo travel
LOCATION:
At #A’s HIDEOUT: XXX - ND.3QQB
CANCEL:
Code‑name #ENDOFWATCH“At #A’s HIDEOUT: XXX – ND.3QQB” What could this be? Back to Marc Steiner’s Medium:
It’s a Mapcode. Replace XXX with FRA and bingo:
And that’s it! After two solid days we finished the CTF. We knew we were top‑16 throughout, but the scoreboard was shuffled.
At one point we even held 2nd place for a while!
Really happy to stand alongside all these big OSINT names!